Settings Checked
IIS Authentication settings
Made sure Anonymous was disabled, Windows Authentication was enabled.
I saw a number of sites that said to bump up NTLM to the top of the Providers list…which isn’t recommended. (Didn’t work anyway.)
Web.config Settings - made sure the settings were correct there:
<authentication mode="Windows" />
<identity impersonate="false" />
Browser-based settings for users who were prompted for credentials:
Also added the app to the Trusted Sites just to make sure.
Solution
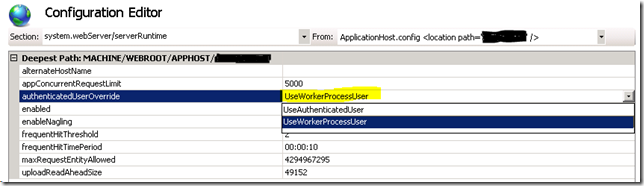
I realized that setting Windows Authentication in IIS causes the current user’s identity to be used when the site’s files are accessed on disk. In the case of the users who were prompted, they weren’t in an AD group that had permission to the root directory. But granting access to the root folder isn’t an option for security reasons, especially if you’re storing a database connection string in the web.config file.Thanks to this post, I learned IIS 7.5 has a setting that forces IIS to utilize another identity for disk access even when Windows Authentication is utilized. The key is to set the authenticatedUserOverride option to use the “UseWorkerProcessUser” value. Of course, make sure the worker process has permissions to the app's directory.